Together with…

Introduction
The decentralisation behind blockchain technologies is bringing incredible evolutions to various economic sectors, including the financial sector. Certainly, the most disruptive innovation of the entire blockchain ecosystem is the possibility of allowing the verification and certification of data without the use of a centralised authority, hence the paradigm of decentralisation, at the base and operation of which is made possible by the presence of so-called consensus algorithms.
These technologies are able to guarantee immutability and incorruptibility of information and transitions on the blockchain allowing network users to interact with each other in a trustworthy manner.
Satoshi Nakamoto, unknown creator of Bitcoin, was the developer of the first consensus algorithm of the BTC blockchain, subsequently there were many other blockchains that used the same algorithm called Proof of Work (PoW) and subsequent evolutions that led to the creation of new, more efficient algorithms, such as Proof of Stake and its derivatives, in order to improve some limits present in the original PoW.
The importance of Consensus Algorithms
At the base of each blockchain there is always a consensus algorithm whose function is to verify and consequently validate the transactions present on the network. A transaction, once inserted in the blockchain, becomes immutable, therefore impossible to modify, to cancel or to counterfeit, thanks to the intervention of the consensus algorithm. In essence, it is the algorithm that “brings together” the various counterparties present on the blockchain and that makes the operation and intrinsic characteristics of this technology possible. Without consensus algorithms blockchains would not exist and without them there would be no cryptocurrencies, nor decentralised services. In a nutshell, these algorithms and their correct functioning guarantee the efficiency and functioning of the entire blockchain, in fact they represent its fundamental core.
Different types of Consensus Algorithms
The first distinction necessary for the correct understanding of blockchains and consequently of the types of algorithms used is the one between:
- permissionless blockchain, in which any user can participate and carry out transactions. There the concept of decentralisation reaches its peak, since there is no central body that can define the rules of the protocol;
- blockchain permission-ed, in which only certain types of previously authorised users can operate and execute transactions. This type of blockchain is partially decentralised, since it is typically privately managed and consequently less secure than the permission-less one.
As mentioned above, at the core of each blockchain there is a consensus algorithm. In this analysis we will consider the main permission-less algorithms, at the basis of the most important and sophisticated blockchains currently on the market:
- Proof of Work (PoW)
- Proof of Stake (PoS)
- Delegated Proof of Stake (DPoS)
- Nominated Proof of Stake (NPoS)
- Proof of History (PoH)
Proof of Work
Introduced in 2008 in Satoshi Nakamoto’s original Bitcoin whitepaper, it is a technology conceived several years earlier and used in cryptographic environments. The Proof of Work (PoW) algorithm has been for years the most used and known algorithm used in the validation of transactions on the blockchain and consequently responsible for the proper functioning of these networks. The primary functionality of the algorithm is to ascertain the correctness of transactions on the blockchain, avoid the problem of double spending (i.e., the possibility of spending the digital asset subject of the transaction more than once) and record each new successfully transaction in the distributed ledger on the blockchain itself.
In practice, cryptographic transactions are not recorded individually in the distributed ledger but are grouped into blocks. Each block contains the set of transactions of a given moment and the block itself, with all the transactions contained therein, needs to be validated, before being permanently registered on the blockchain. The validation operation, the subscription to the distributed ledger and, consequently, the contribution to the growth and maintenance of the network takes place through users, defined as miners, appointed to validate the blocks, who using a specific hardware called ASIC, and provide the necessary computing power defined Hash Power for validation operations. In fact, the algorithm provides for the resolution of a complex mathematical problem in order to generate a Hash, i.e., an output capable of respecting the validation conditions defined by the blockchain itself.
The miners receive a reward in cryptocurrencies, for carrying out this task and the provision of the necessary Hash Power. In the event that the calculated Hash does not meet the conditions set out in the protocol, the miner will have to continue solving Hash functions in order to find the correct Hash for validating the data block in question. Once the correct Hash has been found, the protocol will allow you to update the distributed ledger and the other participants in the network (the other nodes, consisting of other miners) will update their blockchains to include the new block. The entirety of the process just described at the base of the PoW algorithm is called Mining.
The Mining process, and those blockchains that use PoW algorithms, present in facts a considerable security and solidity, directly proportional to the growth of the entire network and consequently of the nodes. The greater the size of the blockchain, the greater the difficulty of tampering with the blocks and therefore the greater the security level. However, precisely because of their intrinsic characteristic in which a “proof of work” is required, as the number of nodes and the size of the blockchain increases, the need for computing power, Hash Power, increases, with consequent waste of energy resources and inefficiencies, resulting from the slow resolution of the Hash by the miners. Furthermore, the recent polarisation of pooled mining activities, often managed by corporations, generates some centralization risks and dangers, which can lead to unpleasant consequences, first of all, the problem relating to a potential attack on the blockchain defined as “51% attack” where, from the theoretical point of view, the concentration of 50% + 1% of the Hash Power in the hands of a coordinated group of miners could allow to take control of the entire network.
Focus on… Hash
A hash function is a unique identifier used in cryptography, a process that transforms data, typically plaintext of any size, into a unique ciphertext of a specific length and specific characteristics. Basically, hashing is a way to ensure that all data sent over a network, such as a blockchain, reaches the correct recipients in the same condition in which it was written, i.e., completely intact and without risk of being corrupted during the transfer.
Focus on… 51%
The 51% attack is usually described as an event where a group or a single person acquires more than 50% of the total computational capacity of the mining. If this happens in a Proof of Work like Bitcoin, it would allow the group or person to change a particular block of the chain for illegal activity. A recent example of this event occurred against the Verge blockchain, where $ 1.75 million in XVG coins was withdrawn at the time of the hack. With the Proof of Stake, there would be no incentives to try to tamper with the network with the 51% attack because in order to carry out the necessary actions for the hack, the user must have staked at least 51% of the total amount of cryptocurrency in the market. To do this, he would have to physically buy the necessary amount of coins on the secondary market. These repeated purchases would have the effect of generating an uncontrolled increase in the price of the coin itself, ending up nullifying any gain deriving from the attack itself.
Proof of Stake
The Proof of Stake (PoS) consensus algorithm was first proposed in 2011 by Sunny King and Scott Nadal, as an alternative method for reaching consensus across nodes. The purpose was to solve the typical problems of the PoW algorithm in which the amount of electricity required for the validation activities is excessively onerous. The PoS algorithm is based on a process of “random election” of a node as a validator of transaction blocks. Users defined as Forgers who wish to participate in this forging process are required to own and maintain a certain amount of tokens within the blockchain that adopts PoS, through a process called staking. In fact, in the Proof of Stake consensus model, the amount of tokens owned by each user assumes relevance within the system: the larger the stake, the greater the probability of being selected as validator nodes, and consequently, the more robust it will be, as the number of nodes grows, the security of the system. This apparently very efficient mechanism could in some cases considerably increase the risk of centralization of the blockchain itself. In fact, one of the risks of this type of protocol is represented by the exclusion of all those nodes which, although adhering to the blockchain, hold an insufficient number of tokens to allow the nomination for a node.
To overcome this problem, in addition to considering the number of tokens owned, two other factors are considered in the process of electing a new node:
- the first, called “CoinAge Selection”, allows you to select nodes on the basis of the holding time of the tokens in stake;
- the second, called “Randomised Block Selection”, is based on the search for potential nodes that have a combination of low Hash values and size of the amount of tokens in staking.
Once the process of selecting a new node has been completed, and before creating the next transaction block, the new node is asked to check the validity of the previous transactions, sign the block present in the network at the time of its entry and add it to the blockchain. The reward due to the forgers for the activity carried out as validating and maintaining nodes of the blockchain based on the PoS algorithm corresponds to a part of the commissions paid by users for each transaction carried out on the network.
One of the most important advantages resulting from the use of the PoS algorithm is the amount of energy and electricity saved, compared to those blockchains that use PoW algorithms. A further interesting feature of the PoS consensus mechanism, capable of significantly increasing the security of the protocols based on it, and discouraging fraudulent behaviours, is that provides for the joint responsibility of the nodes in the face of illegal transactions. In fact, if fraudulent transactions are identified in the blockchain, the node responsible for validating them could be sanctioned by losing a part of its tokens held in stakes as well as the rights to participate as a forger in future selections, an excellent method to discourage malicious behaviour and increase the responsibility of stakers. Even in the case of the PoS, the attack known as “51% attack” turns out to be extremely complex and burdensome to perform, since the attacker should be able to hold the majority of the entire “total token supply” of the blockchain.
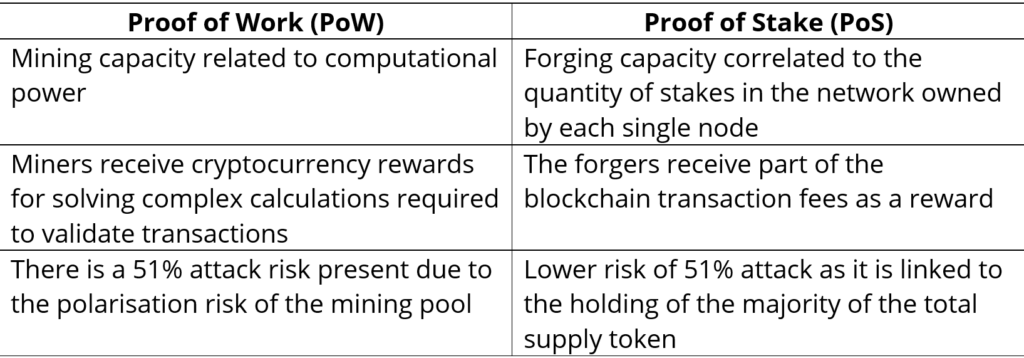
Proof of Work Vs Proof of Stake… a summary
The Proof of Work consensus algorithm, mainly used by more “traditional” cryptocurrencies including Bitcoin, is based on the use of computational power provided by miners and treated in the Mining & Hashrate analysis. PoW proved to be a very robust mechanism but at the same time very expensive in terms of speed and validation of a large number of transactions, as well as very expensive in terms of hardware and energy.
On the contrary, Proof of Stake provides that the validation operations of new blocks are the responsibility of the users holding the token, therefore the investor (token holder and staker of the blockchain itself) becomes an active component, contributing both to increasing security and participating in the maintenance of the entire infrastructure. As described in the previous analysis, therefore, staking is configured as an alternative to mining, faster and more efficient, and not easily subject to malicious attacks such as the 51% attack. This is in fact the main reason why Ethereum, one of the most capitalised blockchains in the market, switched from a PoW system to a PoS system after the ETH 2.0 update called “Serenity”.
Delegated Proof of Stake
A further implementation of the PoS is the Delegated Proof of Stake (DPoS), developed by Daniel Larmier in 2014. It is adopted by blockchains such as BitShares, Steem and EOS and implements interesting innovations for the selection of validators.
In the DPoS system, the burden of confirming transactions does not fall on the entire network, but is a task entrusted to a number of delegates: the major holders of staking tokens have the right to elect delegates in order to validate, make efficient and protect the functioning of the network. The voting power is directly proportional to the number of coins owned by the user. The delegated nodes are responsible for reaching consensus and validating the new blocks. The voting system varies according to the different blockchains that use this consensus algorithm. In principle, the rewards obtained by the delegates are then shared with the respective voters. Therefore, in the case of DPoS, the power conferred by the amount of stake tokens owned is limited exclusively to the election of validator nodes. This system apparently appears very democratic and decentralised; however, the application of a representation system has generated a series of doubts relating to the effective decentralisation: the quantitative aspect once again plays a crucial role that defines the influence of the voter. In fact, whoever has more tokens has greater influence and greater weight in the voting of the delegated nodes.
Nominated Proof of Stake
This consensus algorithm is also a variant of the now known Proof of Stake. In this case there are two main actors: the “Nominators” and the “Validators”. The “Nominators” are the holders of tokens kept staked on the blockchain, which contribute to the security of the network through the “backing” (i.e., the appointment) of up to 16 Validators responsible for the creation of the blocks. The Validators, as already indicated, are appointed by the Nominators, they have the function of creating and validating new blocks and in order to operate in the network they must be in an active set that allows them to perform the assigned functions in turn. It is interesting to note that, since Validators are appointed by Nominators, apparently this role does not directly depend on the number of tokens staking on the blockchain; however, Nominators are directly chosen on the base of the amount of tokens they themselves hold in staking.
The goal of NPoS is to ensure decentralisation, fair representation, and high security through two phenomena:
- proportional justified representation;
- and maximum support (“maximin support”).
The first guarantees the proportionality between the places assigned to the validators and the appointments. Therefore, the greater the number of nominations received and the more considerable the number of tokens staked in support of the validator, the higher the probability of being elected in an active set. As the Nominators cast their votes, the algorithm divides them equally among the validators, to avoid giving more weight to some of them. This mechanism is referred to as “maximin support” and guarantees that validators are in practice “supported” with the same amount of stakes. By doing so, in the NPoS all validators of the active set receive the same reward, from which the commissions dedicated to them are subtracted and the remaining part of the fees is distributed to the Nominators in proportion to the share of tokens deposited in stakes. In fact, the NPoS aims to prevent the potential formation of oligarchies and bad actors who appoint validators through the pure quantitative criterion relating to tokens, giving a voice to minorities too.
To complete the reasoning, we can say that the NPoS consensus algorithm guarantees decentralisation from a technical point of view, while managing to reward the Nominators, as pro-quota staker, that is, on the basis of the investment made initially. It is necessary to mention the fact that Nominators are also exposed to the risk of “slashing” in the eventuality their appointed validators demonstrate incorrect behaviour. This aspect represents the main difference between NPoS and DPoS, where the “delegates” are not subject to this risk, as explained above, since they are delegated directly by the mechanism inherent in the blockchain.
Focus on… NPoS & Polkadot
In the specific case of Polkadot, one of the most interesting blockchains of recent years, the consensus algorithm adopted is the NPoS. However, on this blockchain, there are two additional figures necessary for the proper functioning of the network: the Collators are responsible for maintaining the Parachains (i.e., blockchains of the Polkadot ecosystem parallel to the main Relay Chain), collecting and preparing the transactions that will then be validated by the Validators. Finally, they play an important role in the link between Parachain and Relay Chain.
The Fishermen are in charge of controlling any malicious behaviour which will then be reported to the Validators. This role can be played by full nodes, collators or by the users of the blockchain themselves.
Polkadot: heterogeneous multicultural framework
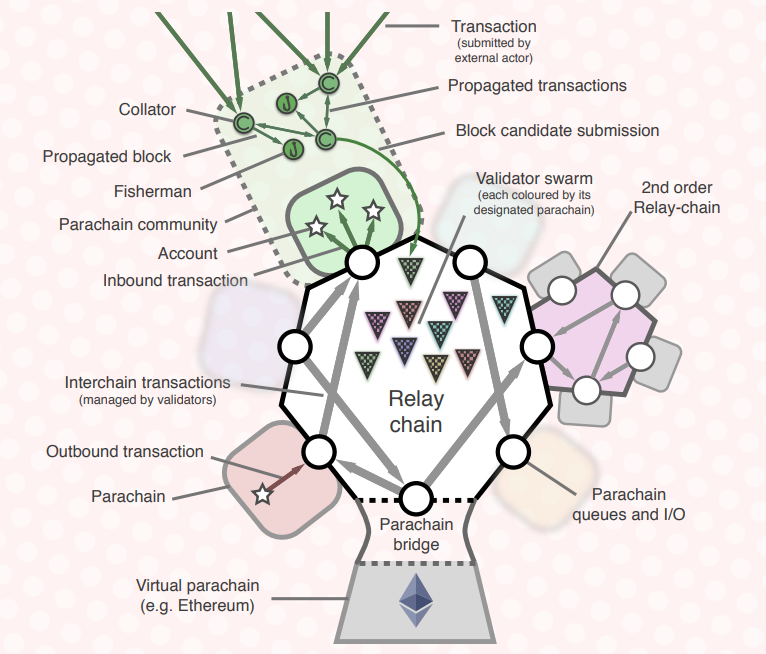
A summary diagram of the Polkadot system, taken directly from the protocol whitepaper, shows how validators collect and propagate user transactions. Furthermore, the figure shows how a user can publish a transaction that is carried out in a parachain (internal to the Polkadot world and external to the parachain bridge), through particular nodes that interact with the Polkadot ecosystem.
Proof of History
The Proof of History algorithm is a computation sequence, implemented in Solana, one of the most interesting third generation blockchains on the market by Anatoly Yakovenko. It should be emphasised that the Proof of History is not a consensus mechanism, it is an implementation of the PoS algorithm capable of speeding up the time required to confirm transactions on the blockchain. Yakovenko, drawing on his own research carried out at Qualcomm, implemented the concept of timing in the PoS consensus algorithm. This has made it possible to approach the solution of the problem identified by Vitalik Buterin himself (founder of Ethereum) called Trilemma, i.e., the need to be able to have within the same blockchain: (1) decentralisation, (2) security and (3) scalability, concepts that are not easy to reconcile.
The main feature of the Proof of History is therefore, the ability to track the order of transactions on the blockchain, which allows for greater speed and ease of selecting a validator for each subsequent block of transactions. In fact, the nodes need less time to validate the order of the transactions. Technically, all transactions on Solana are encrypted (“hashed”) with a SHA256 algorithm, the application of this encryption algorithm generates an output, which Solana uses as input for the subsequent hashed transaction, this allows to integrate in the hashed output the order of each transaction. The application of this technique creates a clear and verifiable order for all transactions without the need for a conventional timestamp. By sorting transactions in a hash chain, validators process and transmit less information in each block which greatly reduces the confirmation time and effectively makes the blockchain faster and more scalable, while maintaining security.
Conclusions and future scenarios
In conclusion, the evolution of the current market suggests a migration of the most important blockchains, excluding Bitcoin (which is increasingly becoming a standard for the conservation of value, store of value, rather than for the decentralised execution of financial services), from PoW to PoS. This choice derives from the need to use more efficient algorithms, especially the increase in the number of transactions due to the growing adoption of certain cryptographic protocols and with them decentralised financial services. The competition to make networks more efficient and solve the so-called trilemma is leading developers from all over the world to further implementations and improvement of the PoS. The transition of Ethereum from proof of work to proof of stake, the presence of third generation blockchains such as Polkadot and Solana, aimed at solving the trilemma in a smart and technically elegant way, leads to imagine a future characterised by intense competition between different based blockchains on PoS protocols and subsequent evolutions.